HIPAA Compliance Essentials: Interactive Guide for Medical Admins
Understanding HIPAA compliance isn't just a checkbox for healthcare providers—it’s a frontline responsibility for medical administrative staff. From verifying patient identity to handling records and communicating with third parties, admins are often the first line of defense in safeguarding protected health information (PHI). The Health Insurance Portability and Accountability Act (HIPAA) doesn’t just apply to doctors and nurses. If you’re scheduling appointments, handling intake forms, or transmitting any sensitive data, your actions must comply with HIPAA’s privacy and security rules—or risk fines, investigations, and data breaches.
This guide is tailored for medical administrative professionals who need a practical, no-fluff understanding of how HIPAA impacts their daily tasks. We’ll walk you through actionable examples, explain where most clinics go wrong, and show how even your login habits can be the difference between compliance and a costly violation. Whether you’re at a front desk, managing digital records, or training new staff, this resource gives you clear insight into how to stay compliant—and how to protect yourself and your clinic in a fast-moving digital landscape.
Why HIPAA Applies to Admins
Medical administrative professionals are classified as workforce members under HIPAA, which makes them directly accountable for how protected health information (PHI) is handled, shared, stored, or transmitted. Admins aren’t just passive recordkeepers—they are often the point of entry for PHI into a healthcare system. Whether you’re collecting insurance cards, updating patient records, or routing a phone call, your actions are regulated by HIPAA. That means violations at the admin level can expose your entire clinic to audits, fines, and public trust loss.
Who is a Covered Entity?
HIPAA regulations apply to covered entities, which include healthcare providers, health plans, and healthcare clearinghouses. But this also extends to business associates—third parties and individuals who perform services involving PHI. If you’re working in a clinic, hospital, dental office, or telehealth startup, chances are you fall under this classification. Even if you’re not licensed medical staff, your admin role still comes under HIPAA governance because you handle patient data, schedule appointments, or transmit records electronically. Ignorance of this classification has led to dozens of reported violations in clinics that didn’t train their front-desk teams adequately.
What Counts as PHI?
Protected Health Information (PHI) includes any patient data that can be used to identify an individual—directly or indirectly. This ranges from names, addresses, and birthdates to insurance numbers, treatment notes, lab results, and even billing information. If the data is connected to a health condition or service and it’s stored or shared electronically, by phone, fax, or paper—it’s PHI. For admins, this means that even checking a patient's appointment over the phone without proper verification can lead to a breach. Many admin mistakes happen due to misunderstanding what counts as PHI, especially in intake forms, voicemails, and sign-in sheets.
Day-to-Day HIPAA Compliance Examples
HIPAA compliance isn’t just about forms and policies—it’s about minute-by-minute decisions admins make while handling phones, emails, front desk interactions, and digital systems. These everyday moments are where most violations occur—not through malicious intent, but due to rushed processes, incomplete training, or outdated habits. By understanding real-world compliance pitfalls, medical admins can protect their patients’ privacy and shield their organizations from serious consequences.
Phone, Fax, Email Scenarios
Answering a call from a “family member” without verifying patient consent? That’s a HIPAA violation. Faxing a referral to the wrong number? Another violation. Emailing lab results without encryption or patient authorization? That’s a breach. Admins must always verify identity before sharing any PHI—regardless of whether the channel feels informal or routine. This includes checking phone access codes, confirming designated contacts, and using secure messaging platforms when transmitting health information. Even voicemails must avoid sharing specifics unless the patient has authorized that mode of communication. Every action should follow the “minimum necessary” standard, disclosing only the essential data for a given task.
Front Desk Privacy Pitfalls
At the front desk, HIPAA violations often happen unintentionally—but the risks are just as real. Calling out full names and conditions in a crowded waiting room, leaving open charts on the counter, or discussing sensitive patient information where others can overhear are all breaches. Sign-in sheets must avoid revealing appointment reasons or provider names. Even computer screens visible to patients while checking in can be problematic if PHI is exposed. Admins should maintain visual barriers, use screen protectors, and avoid engaging in any patient-related discussions where privacy can’t be guaranteed. The front desk is not just a customer service station—it’s a HIPAA-sensitive zone.
HIPAA Security Rules Simplified
The HIPAA Security Rule focuses specifically on protecting electronic PHI (ePHI). For medical admins, this means following technical, administrative, and physical safeguards that keep data protected as it’s stored, transmitted, or accessed. While IT teams build the infrastructure, it's often admins who make or break compliance through their login habits, device use, and data access practices. You don’t need to be a cybersecurity expert—you just need to follow best practices consistently and understand the core principles behind the rules.
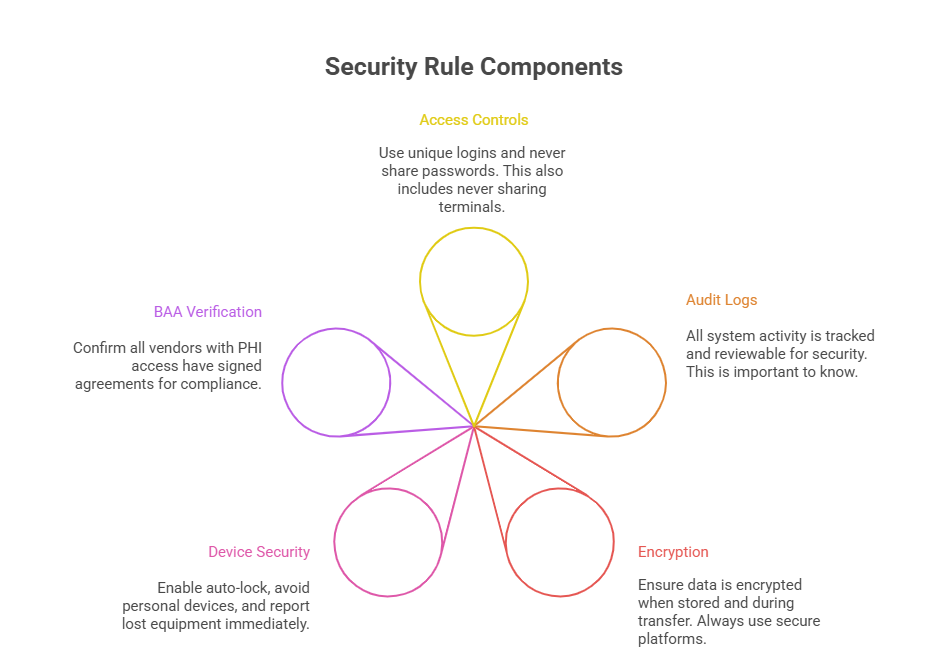
Access Control, Audit Logs, Encryption
Admins should have unique login credentials—no shared logins across staff. Access must be role-based, meaning you only view what you need for your job. Audit logs track every login, document access, and data edit—making it easy to trace suspicious behavior back to specific users. Encryption is non-negotiable: data must be encrypted during storage and transfer. Even a lost tablet or unprotected backup drive can trigger a breach investigation. Clinics should ensure all devices are encrypted and regularly audited. If you're using a practice management system, ask: is data encrypted at rest and in transit? If not, it’s a risk.
How Admins Support Digital Security
Admins support digital security through daily vigilance—logging out when stepping away, reporting suspicious login attempts, and refusing to install unauthorized apps on clinic devices. When onboarding vendors or using new platforms, admins should verify Business Associate Agreements (BAAs) are in place. If you're forwarding ePHI to another provider or patient, always double-check the recipient and method of transmission. Even using your personal phone for work communication without secure messaging apps can result in a violation. Cybersecurity isn't just an IT problem—it's an admin’s daily responsibility too. By creating digital hygiene habits, you contribute directly to HIPAA security compliance.
Violations, Fines & Legal Implications
HIPAA violations don’t just happen in dramatic data breaches—they often result from simple admin missteps: a wrong fax number, a shared password, or an unencrypted file attachment. But the consequences can be severe. Fines range from $100 to $50,000 per violation, with a maximum annual penalty of $1.5 million. Beyond the financial hit, practices risk losing patient trust, facing lawsuits, and triggering federal audits. Most importantly, individual staff—including admins—can face termination if found negligent.
Common Mistakes That Get Flagged
Sharing passwords among front desk or billing staff
Leaving paper charts or sign-in logs visible to patients
Discussing patient conditions within earshot of others
Emailing or texting PHI without encryption
Faxing to outdated or unverified numbers
Using unapproved cloud storage for documents
Logging in for coworkers or leaving sessions open unattended
Many of these mistakes stem from habit, haste, or lack of training—not intent. But intent isn’t a factor in HIPAA fines. If a mistake leads to unauthorized disclosure, it’s a violation. Admins must slow down, verify identities, and always use secure systems.
Real Case Examples From Clinics
In one case, a clinic was fined $85,000 after a receptionist accidentally gave test results to the wrong spouse. Another practice paid $125,000 because admin staff left PHI accessible on a shared tablet without screen lock enabled. In a dental office, an admin’s casual conversation about a patient in the waiting room triggered a patient complaint and full audit. Even posting photos of a front desk on social media—with visible patient info in the background—has resulted in penalties. These examples show that HIPAA violations at the admin level are not rare, and regulators treat them seriously. Vigilance is the only safeguard.
| Violation Type | Example & Impact |
|---|---|
| Unverified Disclosure | A receptionist gave lab results to a caller claiming to be a spouse without verifying identity. The clinic was fined $85,000 and required to retrain all admin staff and update phone verification scripts. |
| Screen Exposure | An unlocked tablet with patient charts was left on the front desk. A visitor took photos, leading to a privacy complaint. The office underwent a HIPAA audit and implemented automatic screen lock policies. |
| Social Media Slip | A staff member posted a front-desk photo on Instagram with visible charts in the background. OCR flagged this as a violation, resulting in a public warning and mandatory corrective action training. |
| Gossip/Overheard Talk | An admin casually mentioned a patient’s diagnosis in the waiting room. A complaint was filed, triggering an internal investigation. The clinic had to reconfigure seating areas to improve verbal privacy. |
| Negligence vs. Malice | Even without bad intent, admin errors like sending faxes to outdated numbers or failing to log out of systems are penalized. HIPAA enforcement is based on outcome and risk, not intent alone. |
Admin SOPs That Ensure HIPAA Compliance
Standard Operating Procedures (SOPs) are the backbone of HIPAA compliance in any clinical setting. For admins, SOPs clarify exactly how and when PHI can be collected, stored, accessed, and shared. Without clear documentation and consistent execution, even the most well-intentioned actions can lead to accidental violations. By establishing detailed SOPs for intake, communication, and digital documentation, medical admins can ensure their tasks meet federal compliance standards every time.
Consent Forms, Logbooks, Access Logs
Consent forms should be updated regularly, signed by the patient, and stored securely—both digitally and physically. Outdated or incomplete forms open clinics to legal risk.
Visitor and vendor logbooks must avoid collecting or exposing PHI. They should only record names, time in/out, and purpose of visit.
Access logs must be maintained for all systems that handle PHI. Every admin must have a unique login, and login history should be auditable at any time. Shared workstations must lock automatically after periods of inactivity to prevent unauthorized access. These logs are a clinic’s best defense if a privacy complaint arises—proving who accessed what and when.
Training & Incident Reporting
Even the most secure clinic will eventually face a HIPAA concern—a suspicious email, a misfiled document, or a verbal slip. What determines liability isn’t just the error, but how your team responds. Every admin should be trained on incident reporting protocols: how to identify a breach, who to notify, and how to document the event. Timely reporting can mitigate fines and show that the organization has a culture of compliance. Clinics should also schedule annual HIPAA refresher training that covers current digital risks (like phishing or unauthorized app use). SOPs should mandate training logs and incident reports as part of daily admin operations—not optional extras.
| SOP Area | Compliance Protocol |
|---|---|
| Consent Forms | Ensure all patient consent forms are current, signed, and stored in both encrypted digital files and locked physical cabinets. Periodically review for expiration or missing fields, and never proceed without verified consent on file. |
| Visitor Logs | Maintain restricted visitor logs that include only name, date, time in/out, and purpose. Avoid capturing any PHI or clinical details. Store logs securely and limit access to authorized staff only. |
| Access Logs | Use role-based, unique login credentials for all staff accessing EHR or billing platforms. Systems should auto-log access history and flag unauthorized attempts. Admins must never share credentials or leave sessions open. |
| Incident Reporting | Report all suspected breaches or data mishandling immediately using an internal incident report form. Include date/time, type of PHI, involved parties, and initial action taken. Early reporting limits liability and supports compliance. |
| Annual Training | Schedule yearly HIPAA training covering updated regulations, phishing threats, and software changes. Require attendance logs and knowledge checks. Include real-world admin scenarios to reinforce proper response behaviors. |
HIPAA Certification Coverage in Our CMAA Program
Admins play a legal role in compliance—and training is the difference between guessing and knowing. That’s why the ACMSO Medical Scribe Certification includes a full HIPAA and data privacy training module tailored for administrative staff. Instead of general lectures, we’ve built this around real-world clinic scenarios: front desk mishandling, faxing errors, and EHR login violations. It’s not theory—it’s what you’ll face on the job, day one.
In the HIPAA module, students learn exactly how to:
Identify PHI across all channels—paper, email, EHR, phone, fax
Implement digital safeguards like auto-lock, secure messaging, and password best practices
Handle patient identity verification with scripts that align with HIPAA verification standards
Respond to suspected breaches with clear, audit-proof documentation
Maintain consent forms, access logs, and incident reports in compliance with OCR standards
HIPAA + Data Privacy Module with Real Scenarios
We designed our compliance module around interactive case studies. You won’t just memorize rules—you’ll walk through simulated calls, emails, and front desk encounters. You’ll learn why saying a patient’s name too loudly could violate privacy, and how to check ID without sounding confrontational. We also cover what to do if PHI is accidentally sent to the wrong contact, how to log the incident, and how to reduce legal exposure for your clinic.
What sets ACMSO apart is that our CMAA certification isn’t limited to administrative theory. We prioritize privacy, cybersecurity awareness, and legal literacy, because these are the soft skills clinics now demand. Graduates of the ACMSO Medical Scribe Certification are not only ready to manage records—they’re ready to protect them. You’ll walk into your first job already trained in HIPAA fundamentals, with documentation to prove it.
Frequently Asked Questions
-
HIPAA directly applies to all workforce members who handle patient data, including non-clinical admin staff. If you answer phones, schedule appointments, process insurance, or access medical records, you’re handling protected health information (PHI)—and that puts you under HIPAA’s scope. Your actions can trigger violations, even if unintentional. That’s why it’s critical to understand the Privacy Rule, Security Rule, and breach protocols. Proper training in verifying identity, minimizing disclosures, and using secure communication channels is essential. Many HIPAA violations happen at the admin level, so compliance training isn’t optional—it’s your legal protection.
-
Protected Health Information (PHI) includes any data that can identify a patient and relates to their health, treatment, or payment. This includes names, birthdates, phone numbers, insurance info, diagnoses, and even email addresses tied to a medical record. If you’re emailing appointment reminders, verifying identity on the phone, or reviewing a billing record, you’re handling PHI. Even internal memos or sticky notes can contain PHI. Admins must use role-based access, encrypt digital data, and never leave sensitive documents or screens visible to unauthorized individuals—even for a moment.
-
Yes. While most HIPAA penalties target organizations, individuals—especially admins—can face disciplinary action, job termination, or civil fines if found negligent or intentionally noncompliant. If you knowingly disclose PHI to an unauthorized person, you could be reported to the Office for Civil Rights (OCR) and investigated. Even unintentional breaches, like misdirected faxes or emails, are reportable incidents. The best protection is proper training, following SOPs, and documenting any suspected breach immediately. Acting promptly reduces risk and shows you’re working in good faith within a compliant framework.
-
To be HIPAA-compliant, a system must meet technical, administrative, and physical safeguard standards. Look for systems that provide access control, audit logging, and encryption (both in transit and at rest). Additionally, vendors handling PHI must sign a Business Associate Agreement (BAA) with your organization. If your messaging, file sharing, or scheduling system doesn’t offer encryption or role-based access, it’s not compliant. Admins should also verify that devices used for work—especially phones and laptops—have password protection and auto-lock enabled. Compliance isn’t just about software—it’s about using it correctly every time.
-
If you accidentally disclose PHI—by phone, email, or otherwise—report the incident immediately to your HIPAA compliance officer or supervisor. Don’t try to delete or hide the mistake. Transparency matters. Document what happened: the date, time, nature of the data, and who received it. The organization must assess whether the breach qualifies for notification to the affected patient(s) and possibly the OCR. In many cases, quick reporting and mitigation can reduce or eliminate penalties. HIPAA compliance is about how you prevent issues—and how quickly you respond when something goes wrong.
-
Yes, but with caution. HIPAA allows leaving voicemails, but only limited information should be included unless the patient has provided written consent for detailed messages. Without consent, your message should avoid mentioning specific diagnoses, procedures, or results. A safe example: “This is XYZ Clinic calling for [patient name]. Please call us back at [number].” If a patient has authorized voicemail communication and specified preferences, you can follow those instructions. All voicemail practices should be covered in patient consent forms and SOPs that every admin is trained on.
-
Yes, but they must follow the “minimum necessary” standard. A sign-in sheet should only collect names and time of arrival—never reason for visit, provider name, or condition. Information on the sheet must not be visible to other patients once filled. For example, some clinics use adhesive sign-in labels that are removed once the patient is called in. Admins should never ask patients to confirm sensitive details out loud in waiting areas. Privacy in shared spaces is part of HIPAA, and violations here are common but avoidable.
Our Verdict
HIPAA compliance isn’t optional—it’s the daily reality of every medical admin’s workflow. From phone calls to logins, every interaction you have with patient data can either protect or expose your clinic. That’s why investing in proper training isn’t just smart—it’s legally necessary. Admins are not exempt from liability, and even minor missteps can trigger audits, fines, or lawsuits.
If you want to avoid risk, boost your credibility, and become indispensable to your clinic, you need real-world HIPAA training built for admins. The ACMSO Medical Scribe Certification delivers exactly that—scenario-based lessons, up-to-date privacy protocols, and documentation that proves you’re ready for the job. Whether you’re new or experienced, this isn’t just about compliance—it’s about control, confidence, and career readiness.
Quick Poll: Which HIPAA compliance area do you find most challenging as a medical admin?